
On Demand Webinars
Copilot Partners: Unlock your opportunities
Our latest On-Demand webinar provides a practical, execution focused walk through the full Copilot partner journey, from early adoption to advanced scenarios.
Data Protection Strategies Series #2
External attacks dominate headlines, but for SMBs, data-related risks often come from within. Whether through inadvertent errors or malicious activity, insider threats can compromise sensitive information, disrupt operations, and create compliance exposure.
Unlike external attacks, these risks are subtle and continuous, making them both difficult to detect and critical to manage.
Our recent study into SMB operations across the region – conducted by Forrester Consulting – indicates a growing awareness of insider risk, with 40% of SMBs intending to adopt Human Risk Management solutions and initiating cybersecurity awareness training programs for staff.
This tracks with the 63% of SMBs ranking the reduction of enterprise and IT risk exposure as a high-to-critical business objective.
While the study does not explicitly quantify how much of that risk comes from internal activity, it is reasonable to correlate a focus on enterprise and IT risk reduction with concern about both external and internal threats.
Taken together, these insights suggest increased awareness amongst SMBs that internal missteps, uncontrolled access, and user behaviour all contribute to operational risk.
This represents an increased need for proactive insider risk solutions and services that can integrate monitoring, governance and security controls to reduce exposure and enhance operational data resilience.
Insider risk encompasses both malicious activity and accidental mistakes, and in either case it often stems from gaps in how data is monitored, organised, and made recoverable. Routine errors, misconfigurations, or improper access can lead to real operational and regulatory risk.
Managing this risk effectively requires more than reactive monitoring; it needs businesses to have structured governance, to classify their data according to sensitivity and criticality, and to maintain secure, verified backups.
The three foundations of Data Protection are:
Without clearly defined ownership, access policies, and control frameworks, SMBs cannot reliably determine who should have access to which data, nor can they enforce consistent security policies.
Governance provides the rules of the road, ensuring that sensitive information is only accessible to authorised users and that deviations are logged and addressed.
Simply knowing that data exists is not enough. SMBs must understand the sensitivity and criticality of each data asset to apply appropriate safeguards. Classifying data allows organisations to prioritise monitoring, apply targeted controls, and enforce protection measures where they matter most. Without classification, insider incidents—whether accidental or intentional—can lead to the exposure or loss of highly critical data, while less sensitive data consumes unnecessary security resources.
Even with governance and classification in place, mistakes or malicious actions can result in data being corrupted, deleted, or otherwise rendered inaccessible. Backups provide a reliable safety net, allowing organisations to restore critical information quickly and minimise operational disruption. Verified, immutable backups ensure that the data is not only available but trustworthy, even if an insider incident compromises primary systems.
By connecting governance, classification, and secure backup practices with monitoring and response capabilities, partners create a cohesive service line that delivers both security and business value.
These foundational requirements need to be mapped to practical solutions that SMBs can adopt, either directly or as part of a partner-managed service.
This ensures that insider risk is addressed in a proactive, measurable, and recoverable way, rather than relying solely on reactive detection.
Solutions that address these areas include:
Provides data classification, sensitivity labelling, and automated Data Loss Prevention (DLP) policies, helping SMBs enforce controls on sensitive assets and establish clear, auditable rules around data access and handling.
Automates retention policies, compliance monitoring, and reporting across SharePoint, Teams, and OneDrive, creating structured governance workflows that reduce exposure and simplify oversight.
Enable verified, immutable backups to ensure that critical data can be recovered quickly in the event of accidental deletion or malicious activity, supporting both IT and enterprise risk reduction objectives.
By integrating these solutions into a partner-led service, SMBs benefit from continuous monitoring, automated policy enforcement, and reliable recovery, transforming insider risk from a silent threat into a manageable and quantifiable aspect of their data protection strategy.
For MSPs and CSPs, insider risk represents a clear value-creation opportunity:
Deploy uSecure and Netwrix to track user behaviour and system changes in real time.
Configure Purview and AvePoint to classify data, apply retention and access controls, and enforce DLP policies.
Ensure Veeam, Acronis, and Wasabi solutions are integrated to provide verified, immutable backups for quick recovery from insider incidents.
Generate automated audit reports to satisfy regulatory requirements and demonstrate reduced IT risk exposure.
Deliver targeted cybersecurity training through uSecure to reinforce safe data-handling practices and reduce accidental risk events.
By advancing beyond reactive controls to holistic insider risk management, partners can help SMBs protect critical data, maintain compliance, and reduce operational risk, whilst creating a differentiated, revenue-generating service line that builds trust and long-term engagement.


On Demand Webinars
Our latest On-Demand webinar provides a practical, execution focused walk through the full Copilot partner journey, from early adoption to advanced scenarios.
Blogs
Catch our comprehensive summary of the highlights from Microsoft Ignite 2025, combined with the resources and links you need to dig into the detail!

Training
In our latest webinar, our in-house Modern Work experts Jye Wong and Ksenia Turner will run you through a practical refresher on Solution Partner Designations; what they are, why they matter and how to get started.

Sales and Marketing
Business leaders don't live in the tools. They live in the outcomes. The metrics they care about most are not always limited to compliance and risk. So how do you connect data protection to the big-ticket objectives, when they're less obvious? Our in-house pre-sales expert, Michael Brooke explains.

Guides and eBooks
As SMBs mature in the Data Protection lifecycle, they need help to optimise spend, reduce the compliance burden and ensure results align to business objectives. The third installment of our Data Protection Playbook series provides practical guidance for partners on how to address emerging pressure and connect ongoing investment to measurable business value.
Training
Copilot Agents: what are they and how do they differ from AI assistants and chatbots? Our in-house Copilot expert Ksenia Turner explains the use cases and service opportunities for partners.

Blogs
Fragmented data protection systems and processes create compliance proof-gaps for SMB customers. Scott Hagenus, Director, Cybersecurity here at Crayon explains.

Guides and eBooks
How can partners help their SMB customers to move from silos of security and continuity to a more cohesive, measurable and insurable data protection framework? The second edition in our Data Protection Playbook series maps out their journey, and yours.

Sales and Marketing
Ever wonder why a pitch has some IT Managers leaning forward, while others glaze over? Michael Brooke, Cybersecurity Pre-Sales Lead offers some insight on how to tune your approach to chime with different technical mindsets.

Vendor Announcements
Copilot for Business has landed at Microsoft Ignite 2025, levelling the GenAI playing field for SMB customers. Learn all about it from our man on the ground, Andreas Bergman.

Press Release

Press Release

Blogs
As cybersecurity and continuity converge in platforms and in practice, partners need new playbooks to address modern Data Protection standards. Our in-house cybersecurity pre-sales lead, Michael Brooke explains why.

Guides and eBooks
What triggers an SMB customer to begin exploring their need for better Data Protection? The first of our four Data Protection Playbooks for partners breaks down how to position and win in the Pre-Adoption and Exploration stage.

Insights
Data Protection priorities are shifting for SMBs. Ramp up your ability to respond with curated insights, articles and resources to help you guide every customer conversation with confidence.

Partner Spotlight
In this Partner Spotlight, Acceltech Managing Director Ivy Tarrobago shares how Crayon’s responsive support enhances client outcomes and business growth.

Whitepapers
Data Protection is a must for all SMBs but how can partners align solution investment with critical business objectives? Our latest paper shows you how.

Press Release
Crayon has been recognised with a huge double win at the CRN Channel Asia awards ceremony.

Insights
All the latest insights, articles and resources on M365 Copilot, curated into one place.

Insights
SMB customers are storing greater volumes of sensitive data in more places than ever. Secure backup and recovery practices are essential to how they protect it.

Partner Spotlight
Bigfish Technology saved AU$20,000 on its annual Microsoft licensing after one call with Crayon and has since built a strong partnership that enabled Bigfish to get access to Crayon’s expertise and vendor ecosystem.

Insights
Insider risk is a subtle and continuous challenge for SMB customers. Turn it into a manageable and quantifiable aspect of their Data Protection strategy.

Blogs
From rethinking backup to governance frameworks and behavioural analytics, what's involved in building a complete Data Protection strategy for SMB customers?
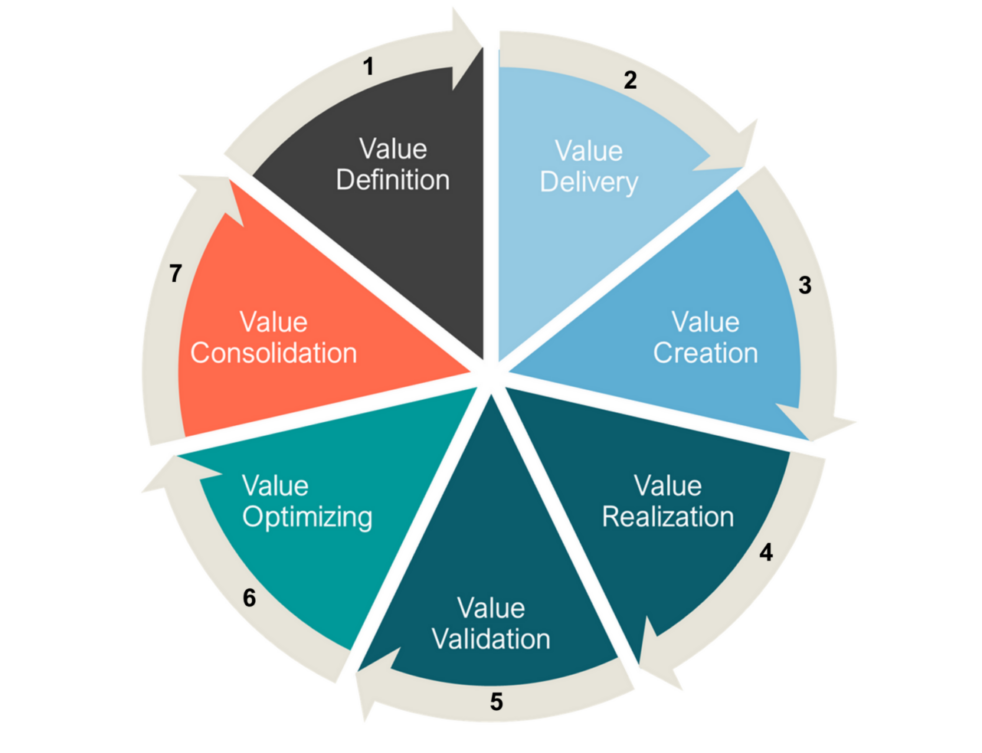
Insights
We explore the evolution of Microsoft's channel strategy over the past ten years, and what can be learned by viewing it through a Value Cycle lens.

Guides and eBooks
The Microsoft Fabric Partner Guide curates our recent articles, videos and resources to accelerate Crayon partner learning.

Press Release
Crayon's commitment to delivering advanced cybersecurity solutions and services takes another step forward as we join the Microsoft Intelligent Security Association.

Insights
Explore how SMBs in APAC are leveraging cybersecurity solutions and AI technologies toward achieving critical business objectives.

Business
Find out why Veeam Immutable Backup is a solution fit for responding to increased demand for optimised security in backup and recovery data.
Case Studies
Working with Crayon, AfterDark scaled its ability to build longer-term cybersecurity engagements with customers.

Webinars Series
Our latest webinar provides a technical deep dive into the advanced security features of Microsoft 365 E5.

Webinars Series
Learn how to help customers cut through cybersecurity overwhelm with strong foundational vulnerability remediation strategies.

Sales and Marketing
Pricing models, service definitions and competitive accelerators. Our latest webinar breaks down how to build a successful MSSP business.

Webinars Series
Practical insights for simplifying cybersecurity service and solution offerings.

Guides and eBooks
Partners, get your Bond on! Our Cyber Operatives Field Guide breaks down five cybersecurity missions to foil would-be cybercriminals.

Insights
The Essential Eight security framework is a pragmatic and clear-cut way for partners to get their customers on the right track when it comes to improved cybersecurity posture.

Podcast
Cybersecurity experts from Crayon, SMX and Red Sift cover the realities of the complex threat landscape and how partners can respond.

Blogs
Crayon cloud security assessments help partners lock down M365 and Azure environments and build profitable cybersecurity practices. Learn how.

Connect Data Protection to strategic objectives via this Whitepaper

What are the most critical business objectives and solution adoption priorities for SMBs in our region? Download the latest Forrester study to find out!

Our APAC channel business is now part of a global organisation. That means there is a whole new world of value on offer for our partners. We can help you to tap into all of it.