
On Demand Webinars
Copilot Partners: Unlock your opportunities
Our latest On-Demand webinar provides a practical, execution focused walk through the full Copilot partner journey, from early adoption to advanced scenarios.
Microsoft 365 E5 is the most comprehensive suite offered by Microsoft, integrating advanced security, compliance, and IT management features. It is designed to help businesses consolidate multiple solutions into one, thereby reducing costs and simplifying IT management.
Over the next hour our session experts will guide you through the Microsoft E5 solution, how to deploy best practices that safeguard data and streamline compliance.
You’ll learn how implementing Microsoft E5 can help to reduce licensing costs by up to 60% and improve IT management efficiencies.
Watch the full webinar below, read on for key takeaways and download the presentation deck for future reference.
![]()
Andrew Aldridge
Pre-sales Technical Specialist, Crayon Channel APAC
Michael Brooke
Solution Architect, Crayon Channel APAC
![]()

Security Specialist, Microsoft Australia

Security Consultant, Microsoft Australia
![]()
Microsoft E5 provides the means to simplify security practices in five significant ways:
Juggling multiple standalone security tools can be both expensive and complex. By switching to Microsoft 365 E5, you get an all-in-one, integrated suite which can greatly reduce licensing costs and contribute to less overall management complexity.
Defender for Office 365 and Defender for Endpoint come with built-in automated investigation and response features. These tools take over repetitive security tasks, freeing your team to focus on higher-priority issues. Plus, automated responses mean threats are dealt with faster than ever.
Using Entra ID’s risk-based conditional access, you can strike the perfect balance between security and convenience. This feature evaluates the risk of each login attempt and adjusts security measures accordingly, keeping data safe without frustrating users.
Poor organisational culture will eat your cybersecurity strategy for breakfast. Tools like attack simulation training in Defender for Office 365 can create opportunities to wrap ongoing services around employee education and simulated training for improved frontline understanding of common tactics such as phishing.
For technical users, the struggle to manage the complex nature of security is real. The leaner the team, the greater the need to do more with less, while avoiding increased concern and stress about cutting corners or missing critical incidents.Microsoft 365 E5 is like having a Swiss Army knife for security and compliance. Its unified dashboard provides a clear view of threats across the IT environment, while risk-based conditional access and automated remediation help small or less specialised security teams keep pace with changing techniques and tools used by attackers.
Plus, the features in the E5 suite are ideal for reducing manual processes related to regulatory and compliance demands.
![]()
Microsoft 365 E5 is available in two tiers in Australia: P1 and P2, each tailored to different organisational needs.
This provides robust security and compliance features, including core tools like Microsoft Defender for Office 365 and advanced threat protection capabilities. It’s a solid choice for organisations seeking essential protection and management features without extensive customisation or advanced analytics.
P1 balances affordability and functionality, making it an ideal jump-on plan for SMB customers with lower maturity in their overall approach to security, and/or where there is insufficient technical expertise to manage and maintain more complex security configurations.
This includes all P1 features but adds more sophisticated capabilities, such as advanced risk-based conditional access, automated investigation and remediation, insider risk management, and advanced eDiscovery.
P2 is designed for businesses with higher security and compliance demands, such as those in regulated industries or with a need for detailed forensic insights.
The choice of plan depends on the client’s specific requirements. P2, however, suits customers with a heightened focus on compliance and proactive threat management. For clients managing sensitive data or working in industries like healthcare or finance, P2 provides the depth of protection and analytics required to meet stringent security and regulatory needs.

On Demand Webinars
Our latest On-Demand webinar provides a practical, execution focused walk through the full Copilot partner journey, from early adoption to advanced scenarios.
Blogs
Catch our comprehensive summary of the highlights from Microsoft Ignite 2025, combined with the resources and links you need to dig into the detail!

Training
In our latest webinar, our in-house Modern Work experts Jye Wong and Ksenia Turner will run you through a practical refresher on Solution Partner Designations; what they are, why they matter and how to get started.

Sales and Marketing
Business leaders don't live in the tools. They live in the outcomes. The metrics they care about most are not always limited to compliance and risk. So how do you connect data protection to the big-ticket objectives, when they're less obvious? Our in-house pre-sales expert, Michael Brooke explains.

Guides and eBooks
As SMBs mature in the Data Protection lifecycle, they need help to optimise spend, reduce the compliance burden and ensure results align to business objectives. The third installment of our Data Protection Playbook series provides practical guidance for partners on how to address emerging pressure and connect ongoing investment to measurable business value.
Training
Copilot Agents: what are they and how do they differ from AI assistants and chatbots? Our in-house Copilot expert Ksenia Turner explains the use cases and service opportunities for partners.

Blogs
Fragmented data protection systems and processes create compliance proof-gaps for SMB customers. Scott Hagenus, Director, Cybersecurity here at Crayon explains.

Guides and eBooks
How can partners help their SMB customers to move from silos of security and continuity to a more cohesive, measurable and insurable data protection framework? The second edition in our Data Protection Playbook series maps out their journey, and yours.

Sales and Marketing
Ever wonder why a pitch has some IT Managers leaning forward, while others glaze over? Michael Brooke, Cybersecurity Pre-Sales Lead offers some insight on how to tune your approach to chime with different technical mindsets.

Vendor Announcements
Copilot for Business has landed at Microsoft Ignite 2025, levelling the GenAI playing field for SMB customers. Learn all about it from our man on the ground, Andreas Bergman.

Press Release

Press Release

Blogs
As cybersecurity and continuity converge in platforms and in practice, partners need new playbooks to address modern Data Protection standards. Our in-house cybersecurity pre-sales lead, Michael Brooke explains why.

Guides and eBooks
What triggers an SMB customer to begin exploring their need for better Data Protection? The first of our four Data Protection Playbooks for partners breaks down how to position and win in the Pre-Adoption and Exploration stage.

Insights
Data Protection priorities are shifting for SMBs. Ramp up your ability to respond with curated insights, articles and resources to help you guide every customer conversation with confidence.

Partner Spotlight
In this Partner Spotlight, Acceltech Managing Director Ivy Tarrobago shares how Crayon’s responsive support enhances client outcomes and business growth.

Whitepapers
Data Protection is a must for all SMBs but how can partners align solution investment with critical business objectives? Our latest paper shows you how.

Press Release
Crayon has been recognised with a huge double win at the CRN Channel Asia awards ceremony.

Insights
All the latest insights, articles and resources on M365 Copilot, curated into one place.

Insights
SMB customers are storing greater volumes of sensitive data in more places than ever. Secure backup and recovery practices are essential to how they protect it.

Partner Spotlight
Bigfish Technology saved AU$20,000 on its annual Microsoft licensing after one call with Crayon and has since built a strong partnership that enabled Bigfish to get access to Crayon’s expertise and vendor ecosystem.

Insights
Insider risk is a subtle and continuous challenge for SMB customers. Turn it into a manageable and quantifiable aspect of their Data Protection strategy.

Blogs
From rethinking backup to governance frameworks and behavioural analytics, what's involved in building a complete Data Protection strategy for SMB customers?
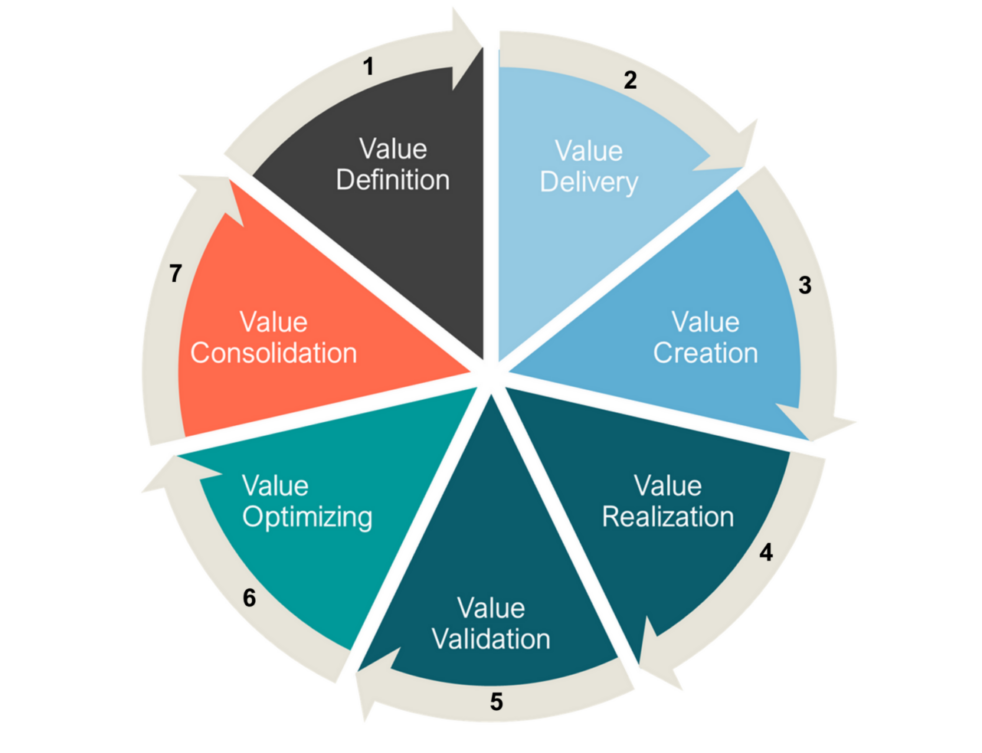
Insights
We explore the evolution of Microsoft's channel strategy over the past ten years, and what can be learned by viewing it through a Value Cycle lens.

Guides and eBooks
The Microsoft Fabric Partner Guide curates our recent articles, videos and resources to accelerate Crayon partner learning.

Sales and Marketing
Pricing models, service definitions and competitive accelerators. Our latest webinar breaks down how to build a successful MSSP business.

Guides and eBooks
Mission essentials for winning data protection business in education, healthcare, retail and manufacturing.

Guides and eBooks
Partners, get your Bond on! Our Cyber Operatives Field Guide breaks down five cybersecurity missions to foil would-be cybercriminals.

Insights
The Essential Eight security framework is a pragmatic and clear-cut way for partners to get their customers on the right track when it comes to improved cybersecurity posture.

Blogs
An explosion in ransomware attacks has fueled a nationwide review of the issue, as concern rises that secret payoffs add increased fuel to the cybercrime fire.
Blogs
Crayon cloud security assessments help partners lock down M365 and Azure environments and build profitable cybersecurity practices. Learn how.

Connect Data Protection to strategic objectives via this Whitepaper

What are the most critical business objectives and solution adoption priorities for SMBs in our region? Download the latest Forrester study to find out!

Our APAC channel business is now part of a global organisation. That means there is a whole new world of value on offer for our partners. We can help you to tap into all of it.