Security 2027: Why ContraForce Stands Out
Looking to provide clients with Managed Detection and Response (MDR) and Managed SIEM services? Read on for six hot takes on why ContraForce should be in consideration.
Six Rock Solid Reasons we like ContraForce
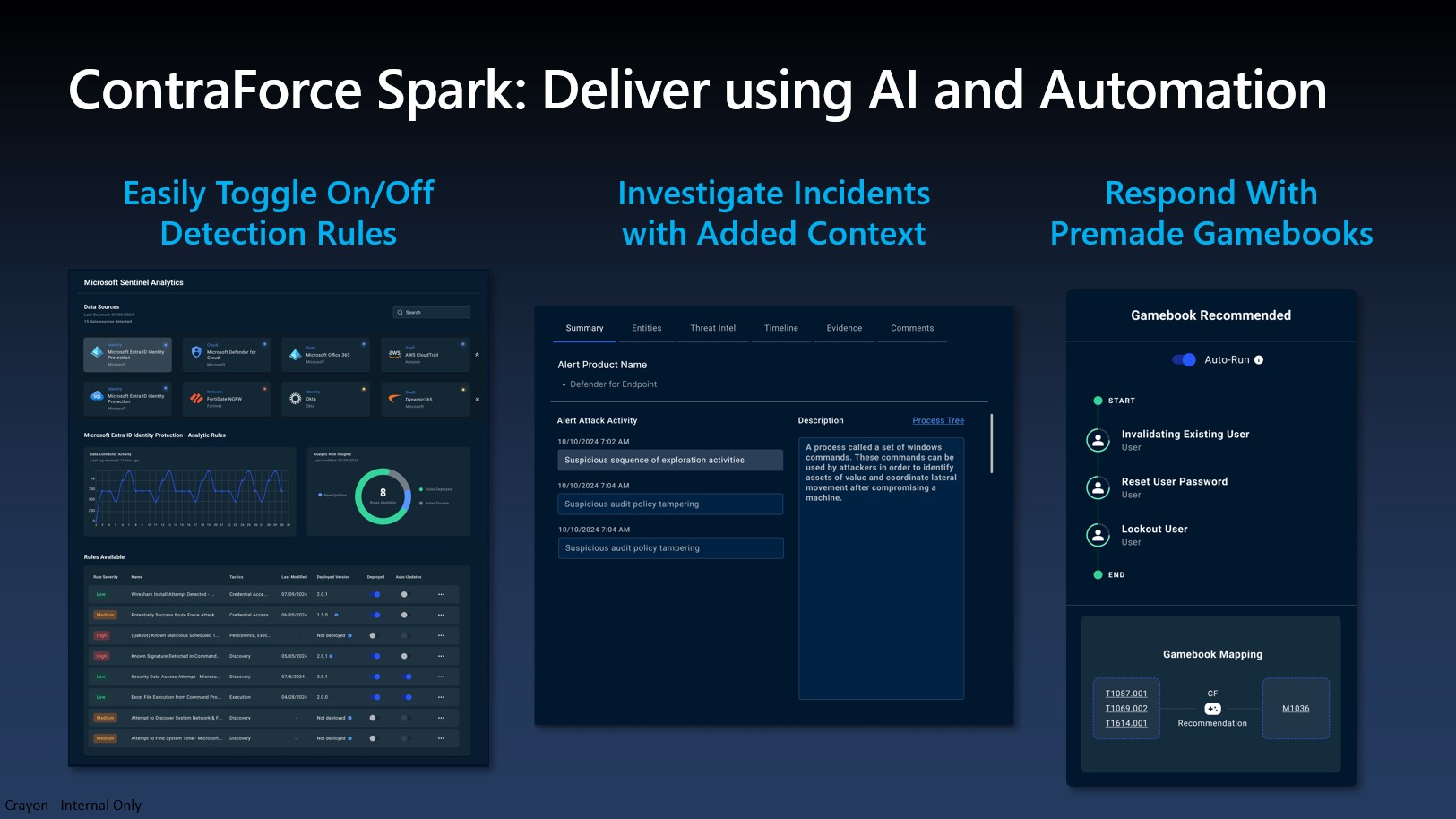
1. API-Based Integration
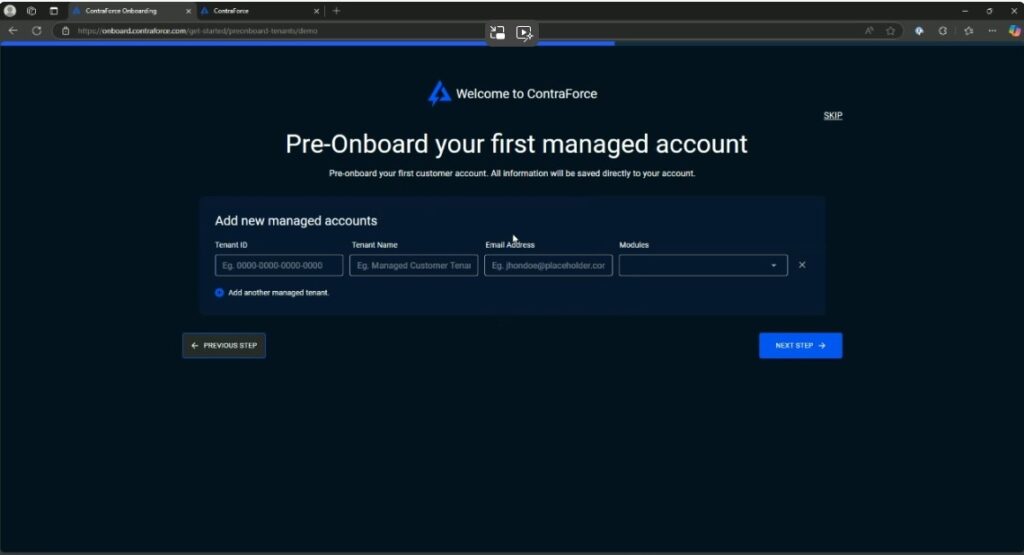
Simplified onboarding and reduced risk are standout benefits of ContraForce and its API-based approach, which eliminates the need for deploying agents. This significantly streamlines the onboarding process. With ContraForce, MSPs can onboard a new client and integrate their existing EDR, SIEM, and ticketing tools in about 15 minutes. This agentless approach not only saves time but also reduces the risk associated with data storage and compliance, as client data remains on-site.
2. Easy move to direct service delivery
ContraForce offers MSPs the flexibility to switch to delivering security services themselves, thereby lowering their monthly costs. This is facilitated through ContraForce Spark, a cloud-based managed service workbench.
3. Service Level Agreements for Enhanced Reliability
Reliability is a critical factor in cybersecurity. ContraForce excels in this area by offering SLAs for detection and response times when MSPs outsource the delivery of security services through the ContraForce Storm commercial program. ContraForce Storm Providers commit to notification times for confirmed security incidents and response times for pre-approved actions, ensuring timely and effective incident management.

4. Leverages Existing Security Investments
Organisations often have existing security tools in place, and ContraForce allows them to maximize these investments. ContraForce integrates seamlessly with leading EDR tools like Microsoft Defender, Crowdstrike, and SentinelOne, as well as SIEM tools such as Microsoft Sentinel, QRadar, and Splunk.
5. No Long-Term Commitments
Flexibility in contractual agreements is another area where ContraForce shines. All ContraForce offerings are available on a month-to-month basis with no long-term commitments. This is particularly advantageous for MSPs who prefer not to be locked into lengthy contracts.
6. Minimising Channel Conflict
ContraForce takes proactive steps to reduce potential channel conflict. Storm Providers are contractually obligated not to share their name or trademark with a client without the MSP’s express prior written consent. Additionally, they agree not to solicit a client for 12 months after the termination of service.
Watch the Demo
Check out this great demo and see for yourself how easy it is to manage customer incidents with ContraForce!
An Easy Decision in a Complex Landscape.
Choosing the right mix of cybersecurity vendors and solutions can be complex.
ContraForce simplifies things with great technology backed by solid service delivery, contract term flex, and no risk of head-to-head compete.
To find out more about how ContraForce can enhance operational efficiency, control and reliability in managing your clients’ cybersecurity needs, visit the ContraForce page on this site, or ask your Crayon account representative to set up time to discuss.
Related

On Demand Webinars
Copilot Partners: Unlock your opportunities
Our latest On-Demand webinar provides a practical, execution focused walk through the full Copilot partner journey, from early adoption to advanced scenarios.
Blogs
Microsoft Ignite 2025: the ‘need-to-know’ highlights
Catch our comprehensive summary of the highlights from Microsoft Ignite 2025, combined with the resources and links you need to dig into the detail!

Training
Modern Work Solution Partner Designations Webinar
In our latest webinar, our in-house Modern Work experts Jye Wong and Ksenia Turner will run you through a practical refresher on Solution Partner Designations; what they are, why they matter and how to get started.

Sales and Marketing
Data Protection for Business Leadership
Business leaders don't live in the tools. They live in the outcomes. The metrics they care about most are not always limited to compliance and risk. So how do you connect data protection to the big-ticket objectives, when they're less obvious? Our in-house pre-sales expert, Michael Brooke explains.

Guides and eBooks
Data Protection Playbook #3
As SMBs mature in the Data Protection lifecycle, they need help to optimise spend, reduce the compliance burden and ensure results align to business objectives. The third installment of our Data Protection Playbook series provides practical guidance for partners on how to address emerging pressure and connect ongoing investment to measurable business value.
Training
Copilot Agents: Level up from chatbots
Copilot Agents: what are they and how do they differ from AI assistants and chatbots? Our in-house Copilot expert Ksenia Turner explains the use cases and service opportunities for partners.

Blogs
Proving Data Protection Compliance
Fragmented data protection systems and processes create compliance proof-gaps for SMB customers. Scott Hagenus, Director, Cybersecurity here at Crayon explains.

Sales and Marketing
Data Protection Sales
Ever wonder why a pitch has some IT Managers leaning forward, while others glaze over? Michael Brooke, Cybersecurity Pre-Sales Lead offers some insight on how to tune your approach to chime with different technical mindsets.

Guides and eBooks
Data Protection Playbook #2
How can partners help their SMB customers to move from silos of security and continuity to a more cohesive, measurable and insurable data protection framework? The second edition in our Data Protection Playbook series maps out their journey, and yours.

Vendor Announcements
Copilot for Business
Copilot for Business has landed at Microsoft Ignite 2025, levelling the GenAI playing field for SMB customers. Learn all about it from our man on the ground, Andreas Bergman.

Press Release
Crayon recognized as the winner of the 2025 Microsoft Asia Partner of the Year Award

Press Release
Crayon recognized as the winner of the 2025 Microsoft Malaysia Partner of the Year Award

Blogs
Data Protection Partner Playbooks for SMB Customers
As cybersecurity and continuity converge in platforms and in practice, partners need new playbooks to address modern Data Protection standards. Our in-house cybersecurity pre-sales lead, Michael Brooke explains why.

Guides and eBooks
Data Protection Playbook #1
What triggers an SMB customer to begin exploring their need for better Data Protection? The first of our four Data Protection Playbooks for partners breaks down how to position and win in the Pre-Adoption and Exploration stage.

Insights
Data Protection Resource Round-Up
Data Protection priorities are shifting for SMBs. Ramp up your ability to respond with curated insights, articles and resources to help you guide every customer conversation with confidence.

Partner Spotlight
The strong, supportive partnership driving Acceltech’s growth
In this Partner Spotlight, Acceltech Managing Director Ivy Tarrobago shares how Crayon’s responsive support enhances client outcomes and business growth.

Whitepapers
Strengthening Data Protection for SMBs
Data Protection is a must for all SMBs but how can partners align solution investment with critical business objectives? Our latest paper shows you how.

Press Release
Crayon wins at CRN Channel Awards Asia 2025
Crayon has been recognised with a huge double win at the CRN Channel Asia awards ceremony.

Insights
M365 Copilot Hub
All the latest insights, articles and resources on M365 Copilot, curated into one place.

Insights
Secure Backup and Recovery
SMB customers are storing greater volumes of sensitive data in more places than ever. Secure backup and recovery practices are essential to how they protect it.

Partner Spotlight
Crayon Expertise: Why Bigfish is hooked
Bigfish Technology saved AU$20,000 on its annual Microsoft licensing after one call with Crayon and has since built a strong partnership that enabled Bigfish to get access to Crayon’s expertise and vendor ecosystem.

Insights
Insider Risk: SMB data and the threat within
Insider risk is a subtle and continuous challenge for SMB customers. Turn it into a manageable and quantifiable aspect of their Data Protection strategy.

Blogs
Data Protection for SMBs
From rethinking backup to governance frameworks and behavioural analytics, what's involved in building a complete Data Protection strategy for SMB customers?
Insights
Microsoft’s Channel Evolution
We explore the evolution of Microsoft's channel strategy over the past ten years, and what can be learned by viewing it through a Value Cycle lens.

Guides and eBooks
The Microsoft Fabric Partner Guide
The Microsoft Fabric Partner Guide curates our recent articles, videos and resources to accelerate Crayon partner learning.

Insights
SMB Strategic Objectives
Small to medium-sized businesses in the APAC region are gearing up tech investments to drive outcomes for customer experience, revenue, business adaptability and innovation. How will SMBs leverage emerging technologies to achieve their strategic objectives?

Insights
Future of Operations 2025
What are the most critical business objectives and solution adoption priorities for SMBs in our region? Download the latest Forrester study to find out!
Case Studies
Crayon Security Assessment service delivers growth for AfterDark
Working with Crayon, AfterDark scaled its ability to build longer-term cybersecurity engagements with customers.

Vendor Announcements
EA to CSP Transition Made Easy
Microsoft changes to its licensing programs means some customers will not be able to renew EAs. Find out how to transition them to CSP in hours, with no disruption or upfront cost, only with Crayon.

Sales and Marketing
How to Design your Copilot Offer
Practical tips for crafting and activating a compelling Copilot GTM proposition.

On Demand Webinars
Security Assessments: Identify hidden revenue potential
Watch this interactive webinar as the Crayon team discuss how to identify and harness hidden revenue potential with Security Assessments.

Training
Copilot for M365 Implementations: Key Risk Considerations for Partners
M365 Copilot implementations for customers should be viewed through a risk tolerance lens. Explore risk tolerance profiles and what they mean.

Webinars Series
Microsoft E5: Do more security and compliance with less
Our latest webinar provides a technical deep dive into the advanced security features of Microsoft 365 E5.

Webinars Series
Master Modern Security with Microsoft Defender XDR and ContraForce
The webinar highlighted the capabilities of Microsoft Defender XDR and ContraForce in providing comprehensive security coverage.


Training
How to get started with VMware Cloud Foundation
Walk through the features of VMware Cloud Foundation and why it is a key tool for Crayon’s cloud partners.

Webinars Series
How to build a simplified cybersecurity practice
Practical insights for simplifying cybersecurity service and solution offerings.

Insights
The critical value of the Essential Eight security framework
The Essential Eight security framework is a pragmatic and clear-cut way for partners to get their customers on the right track when it comes to improved cybersecurity posture.



