Blogs
Microsoft Ignite 2025: the ‘need-to-know’ highlights
Catch our comprehensive summary of the highlights from Microsoft Ignite 2025, combined with the resources and links you need to dig into the detail!

Ransomware poses a huge cybersecurity risk that SMBs need to address. The good news is SMBs can minimise risk by adopting a simple, proven strategy. The Essential Eight cybersecurity framework created by the Australian Cyber Security Centre (ACSC) was built upon strong foundations derived from the globally recognised CIS Control framework. Its purpose is to massively reduce SMB exposure to ransomware attacks as well as other cybersecurity threats.
For SMBs at the start of their cyber security journey, the Essential Eight removes a lot of the planning and complexity because ACSC cyber security experts have done most of the thinking and planning for you. They’ve identified the major threats and listed actions to mitigate them. It’s a joined-up cyber security action plan. For cost-conscious SMBs, the good news is the Essential Eight is free expert consultancy.
Let’s be honest, many SMB owners who are building their business, adding new clients, managing cash flow and growing their team to support expanded operations don’t see cybersecurity as a high priority. They’re focusing scarce time and resources planning the next marketing campaign or new product that can grow the business. Not so much about the stuff that could derail it – like cybercrime generally and ransomware specifically.
One of the challenges for SMBs in accepting ransomware as a risk is the terminology sounds like something out of a crime novel – more like fiction than fact. The hard facts are that ransomware is all too real, and is a direct threat to SMBs in Australia. SMBs need to face that fact and take action.
The ACSC’s annual cyber crime report states the agency received “nearly 500 ransomware cybercrime reports, an increase of nearly 15 per cent from the previous financial year.” Harvard Business Review says ransomware is growing even more quickly: by 150% in 2020 and even faster in 2021.
The ACSC also reports the average downtime caused by ransomware attacks due to recovery of data and restoring networks is 16.2 days – which would be devastating for most businesses.
Ransomware statistics can be scary, but they don’t reveal the horror nor human suffering behind the numbers. Every so often, though, we get a glimpse into the wreckage.
The author of this blog had direct experience of a ransomware victim just recently during an Uber ride. The Uber driver (we’ll call him Joe), explained he doesn’t normally work as an Uber driver. But Joe was forced into a temporary career change when his business was destroyed by cyber attacks – two of them within 3 months. Joe’s successful online business – as a broker between used car vendors and buyers – subsequently went belly up. He and his three staff lost their livelihoods.
The first attack was a ransomware intrusion that encrypted his files including customer, product and financial data. The cyber attacker demanded money to unlock the data. Joe refused to pay, and employed an external specialist who managed to unlock most of the data so Joe could continue his business, albeit with some disruption. A lucky escape!
The second attack was a repeat ransomware attack 3 months later. Joe had done nothing in the meantime to harden his business against cyber attacks. Again, Joe refused to pay, and again employed an external specialist. But this time there was no data left to retrieve – the attacker had deleted it (and probably exfiltrated it to access financial data or customer credit card information). Joe said that at this point he’d have reluctantly paid the ransom ($40K) but he didn’t have cash to do so. Joe’s business was dead.
SMBs like Joe’s can implement security mitigations complying with all eight of the ACSC’s Essential Eight security framework. If Joe had done so, he would almost certainly still be in business today. If he’d even implemented just a couple of measures he’d have substantially reduced his risk. The following two mitigations from the Essential Eight provide an example of effective risk management that would have given Joe’s business a better chance of survival – and the same is true for all SMBs.
![]()
This mitigation action calls for regular data and systems backups (at least daily). Many online businesses – like Joe’s – need more frequent backups so they can restore systems and data to a very recent position. SMBs should implement a backup frequency that suits their specific conditions.
This mitigation also recommends regular testing of the recovery process. Testing proves that the backup solution works, and that data can be restored in the event of a ransomware or other attack. If Joe had implemented this he might have had to lose up to a day’s worth (or less) of data – which would have impacted but not destroyed his business.
![]()
The ACSC says: “Multi-factor authentication is one of the most effective controls an organisation can implement to prevent an adversary from gaining access to a device or network and accessing sensitive information.”
MFA forces users (whether inside or outside the organisation) to provide two or more types of authentication (e.g. username and password, plus a finger or eye scan, or a PIN texted to their phone). MFA makes it much harder for hackers to get access to a system through stolen login credentials – which is likely how Joe’s attacker gained access to his system and data.
These above actions describe just two of the eight recommended mitigations. When SMBs follow the actions and metrics for each of the eight mitigations, it builds up to a comprehensive, joined-up security strategy that can foil ransomware plotters and keep cyber crime at arms length.
The Essential Eight is the outcome of some serious thinking by highly talented ACSC cyber security experts and provides a practical and realistic starting point for many SMBs to prevent ransomware and other attacks. The fact that it’s also free just makes it even more compelling.
Thanks for subscribing to news and update related to Cyber security strategies.
Blogs
Catch our comprehensive summary of the highlights from Microsoft Ignite 2025, combined with the resources and links you need to dig into the detail!

Training
In our latest webinar, our in-house Modern Work experts Jye Wong and Ksenia Turner will run you through a practical refresher on Solution Partner Designations; what they are, why they matter and how to get started.

Sales and Marketing
Business leaders don't live in the tools. They live in the outcomes. The metrics they care about most are not always limited to compliance and risk. So how do you connect data protection to the big-ticket objectives, when they're less obvious? Our in-house pre-sales expert, Michael Brooke explains.

Guides and eBooks
As SMBs mature in the Data Protection lifecycle, they need help to optimise spend, reduce the compliance burden and ensure results align to business objectives. The third installment of our Data Protection Playbook series provides practical guidance for partners on how to address emerging pressure and connect ongoing investment to measurable business value.
Training
Copilot Agents: what are they and how do they differ from AI assistants and chatbots? Our in-house Copilot expert Ksenia Turner explains the use cases and service opportunities for partners.

Blogs
Fragmented data protection systems and processes create compliance proof-gaps for SMB customers. Scott Hagenus, Director, Cybersecurity here at Crayon explains.

Guides and eBooks
How can partners help their SMB customers to move from silos of security and continuity to a more cohesive, measurable and insurable data protection framework? The second edition in our Data Protection Playbook series maps out their journey, and yours.

Sales and Marketing
Ever wonder why a pitch has some IT Managers leaning forward, while others glaze over? Michael Brooke, Cybersecurity Pre-Sales Lead offers some insight on how to tune your approach to chime with different technical mindsets.

Vendor Announcements
Copilot for Business has landed at Microsoft Ignite 2025, levelling the GenAI playing field for SMB customers. Learn all about it from our man on the ground, Andreas Bergman.

Press Release

Press Release

Blogs
As cybersecurity and continuity converge in platforms and in practice, partners need new playbooks to address modern Data Protection standards. Our in-house cybersecurity pre-sales lead, Michael Brooke explains why.

Guides and eBooks
What triggers an SMB customer to begin exploring their need for better Data Protection? The first of our four Data Protection Playbooks for partners breaks down how to position and win in the Pre-Adoption and Exploration stage.

Insights
Data Protection priorities are shifting for SMBs. Ramp up your ability to respond with curated insights, articles and resources to help you guide every customer conversation with confidence.

Partner Spotlight
In this Partner Spotlight, Acceltech Managing Director Ivy Tarrobago shares how Crayon’s responsive support enhances client outcomes and business growth.

Whitepapers
Data Protection is a must for all SMBs but how can partners align solution investment with critical business objectives? Our latest paper shows you how.

Press Release
Crayon has been recognised with a huge double win at the CRN Channel Asia awards ceremony.

Insights
All the latest insights, articles and resources on M365 Copilot, curated into one place.

Insights
SMB customers are storing greater volumes of sensitive data in more places than ever. Secure backup and recovery practices are essential to how they protect it.

Partner Spotlight
Bigfish Technology saved AU$20,000 on its annual Microsoft licensing after one call with Crayon and has since built a strong partnership that enabled Bigfish to get access to Crayon’s expertise and vendor ecosystem.

Insights
Insider risk is a subtle and continuous challenge for SMB customers. Turn it into a manageable and quantifiable aspect of their Data Protection strategy.

Blogs
From rethinking backup to governance frameworks and behavioural analytics, what's involved in building a complete Data Protection strategy for SMB customers?
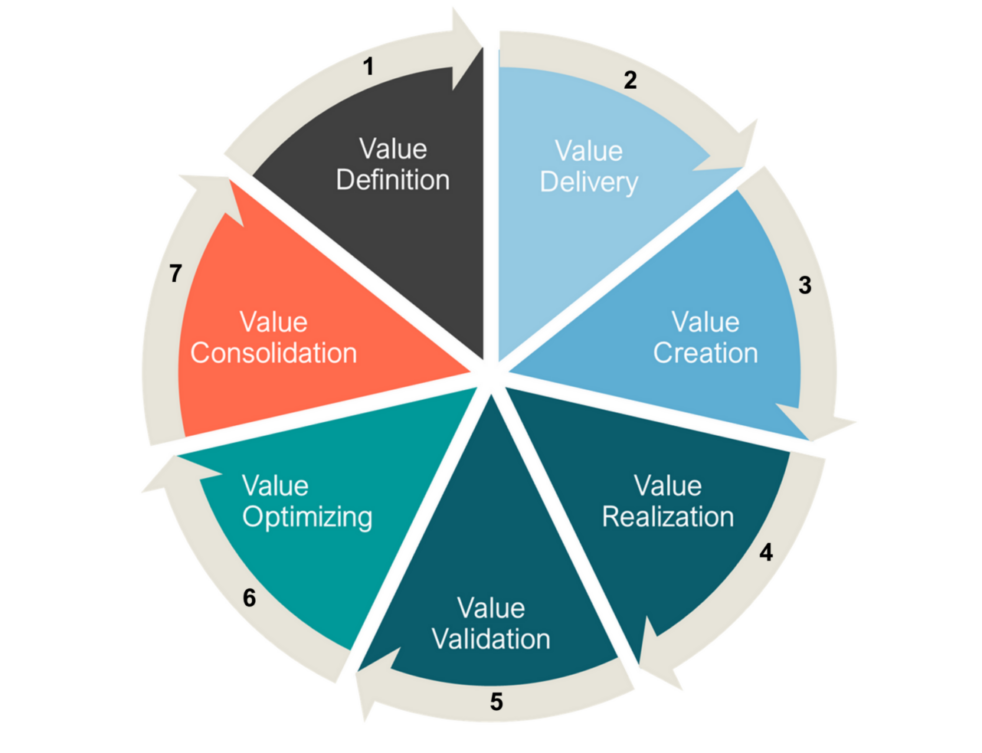
Insights
We explore the evolution of Microsoft's channel strategy over the past ten years, and what can be learned by viewing it through a Value Cycle lens.

Guides and eBooks
The Microsoft Fabric Partner Guide curates our recent articles, videos and resources to accelerate Crayon partner learning.

Insights
Support your cybersecurity game plans with our top picks of new and updated risk and resilience resources.

Blogs

Blogs

Connect Data Protection to strategic objectives via this Whitepaper

What are the most critical business objectives and solution adoption priorities for SMBs in our region? Download the latest Forrester study to find out!

Our APAC channel business is now part of a global organisation. That means there is a whole new world of value on offer for our partners. We can help you to tap into all of it.