
On Demand Webinars
Copilot Partners: Unlock your opportunities
Our latest On-Demand webinar provides a practical, execution focused walk through the full Copilot partner journey, from early adoption to advanced scenarios.
The Essential Eight is a widely used framework to help businesses identify the most common security threats, assess risk levels for each threat, and put mitigations in place for the eight most common vulnerabilities in their networks.
The Australian Cyber Security Centre (ACSC)* developed these prioritised mitigation strategies to provide businesses with clear guidance on how to mitigate cyber threats and incidents. Crayon’s cybersecurity specialist subsidary, emt Distribution can assist your organisation to evaluate the effectiveness and maturity level of all the Essential Eight security controls.
Conduct discovery workshops to collect relevant evidence and identify current baseline.

Review the gathered data, identify risk and compare it to highlight maturity gaps according to the ACSC Essential Eight.

Deliver the executive report highlighting the effectiveness of the controls, with emphasis on those that need immediate remediation based on risk categories: PREVENT, LIMIT and RECOVER.

Outcome based workshops. Timelines vary depending on maturity level assessment focus area.
Detailed reports provide a clear view of findings per control, priority actions and recommendations.
Partners have the options to white label the assessment or position as an independent third-party service.
Experienced regional assessors backed by a global team of cybersecurity experts.

Working with Crayon’s channel team provides partners with advantages, whether they want to gain traction in this domain or scale an existing cybersecurity practice. Partners can leverage the assessment service to support ongoing conversations with customers, and bring their own services, or allied partners with cybersecurity expertise to the table. Equally, partners with mature cybersecurity practices can utilise Crayon’s service to provide account coverage and build pipeline for future works.
Whatever the scenario for your business, our team offers an end-to-end service that can help you take your customers from initial assessment to project scope, solution consulting and full implementation.

The ASD Essential Eight is a cybersecurity framework developed by the Australian Signals Directorate (ASD) to help organizations mitigate cyber threats and enhance their cybersecurity posture.
The Essential Eight comprises eight key strategies that organisations can implement to mitigate the most common cybersecurity threats. These strategies include application allowlisting, patching applications, configuring Microsoft Office macro settings, user application hardening, restricting administrative privileges, patching operating systems, multi-factor authentication, and daily backups.
The Essential Eight provides organisations with a set of practical, actionable strategies to enhance their cybersecurity defenses and protect against a wide range of cyber threats, including malware, ransomware, and phishing attacks.
The ASD Essential Eight framework is relevant to a wide range of organisations, including government agencies, businesses, educational institutions, and non-profits. Any organisation that handles sensitive information or relies on digital systems to conduct business can benefit from implementing the Essential Eight strategies.
Organisations can implement the Essential Eight framework by assessing their current cybersecurity posture, identifying gaps and areas for improvement, and then systematically implementing the eight mitigation strategies outlined in the framework. This may involve deploying security controls, configuring systems, educating staff, and monitoring for compliance.
Implementing the Essential Eight framework can help organisations to strengthen their cybersecurity defenses, reduce the risk of security breaches and data loss, enhance regulatory compliance, improve incident response capabilities, and protect their reputation and brand.
While compliance with the ASD Essential Eight framework is not mandatory, it is highly recommended for organisations looking to improve their cybersecurity posture and protect against cyber threats effectively. Many government agencies and industry regulators also require compliance with the Essential Eight as part of their cybersecurity requirements.
Organisations should regularly review and update their implementation of the Essential Eight framework to ensure it remains effective against evolving cyber threats and changes in their operating environment. This may involve conducting regular security assessments, performing risk assessments, and staying informed about emerging threats and best practices in cybersecurity.
Register your details to book a time to speak to one of our experts on how Crayon Services can help you.
Thanks for contacting Crayon. A team member will reach out to you soon.

On Demand Webinars
Our latest On-Demand webinar provides a practical, execution focused walk through the full Copilot partner journey, from early adoption to advanced scenarios.
Blogs
Catch our comprehensive summary of the highlights from Microsoft Ignite 2025, combined with the resources and links you need to dig into the detail!

Training
In our latest webinar, our in-house Modern Work experts Jye Wong and Ksenia Turner will run you through a practical refresher on Solution Partner Designations; what they are, why they matter and how to get started.

Sales and Marketing
Business leaders don't live in the tools. They live in the outcomes. The metrics they care about most are not always limited to compliance and risk. So how do you connect data protection to the big-ticket objectives, when they're less obvious? Our in-house pre-sales expert, Michael Brooke explains.

Guides and eBooks
As SMBs mature in the Data Protection lifecycle, they need help to optimise spend, reduce the compliance burden and ensure results align to business objectives. The third installment of our Data Protection Playbook series provides practical guidance for partners on how to address emerging pressure and connect ongoing investment to measurable business value.
Training
Copilot Agents: what are they and how do they differ from AI assistants and chatbots? Our in-house Copilot expert Ksenia Turner explains the use cases and service opportunities for partners.

Blogs
Fragmented data protection systems and processes create compliance proof-gaps for SMB customers. Scott Hagenus, Director, Cybersecurity here at Crayon explains.

Guides and eBooks
How can partners help their SMB customers to move from silos of security and continuity to a more cohesive, measurable and insurable data protection framework? The second edition in our Data Protection Playbook series maps out their journey, and yours.

Sales and Marketing
Ever wonder why a pitch has some IT Managers leaning forward, while others glaze over? Michael Brooke, Cybersecurity Pre-Sales Lead offers some insight on how to tune your approach to chime with different technical mindsets.

Vendor Announcements
Copilot for Business has landed at Microsoft Ignite 2025, levelling the GenAI playing field for SMB customers. Learn all about it from our man on the ground, Andreas Bergman.

Press Release

Press Release

Blogs
As cybersecurity and continuity converge in platforms and in practice, partners need new playbooks to address modern Data Protection standards. Our in-house cybersecurity pre-sales lead, Michael Brooke explains why.

Guides and eBooks
What triggers an SMB customer to begin exploring their need for better Data Protection? The first of our four Data Protection Playbooks for partners breaks down how to position and win in the Pre-Adoption and Exploration stage.

Insights
Data Protection priorities are shifting for SMBs. Ramp up your ability to respond with curated insights, articles and resources to help you guide every customer conversation with confidence.

Partner Spotlight
In this Partner Spotlight, Acceltech Managing Director Ivy Tarrobago shares how Crayon’s responsive support enhances client outcomes and business growth.

Whitepapers
Data Protection is a must for all SMBs but how can partners align solution investment with critical business objectives? Our latest paper shows you how.

Press Release
Crayon has been recognised with a huge double win at the CRN Channel Asia awards ceremony.

Insights
All the latest insights, articles and resources on M365 Copilot, curated into one place.

Insights
SMB customers are storing greater volumes of sensitive data in more places than ever. Secure backup and recovery practices are essential to how they protect it.

Partner Spotlight
Bigfish Technology saved AU$20,000 on its annual Microsoft licensing after one call with Crayon and has since built a strong partnership that enabled Bigfish to get access to Crayon’s expertise and vendor ecosystem.

Insights
Insider risk is a subtle and continuous challenge for SMB customers. Turn it into a manageable and quantifiable aspect of their Data Protection strategy.

Blogs
From rethinking backup to governance frameworks and behavioural analytics, what's involved in building a complete Data Protection strategy for SMB customers?
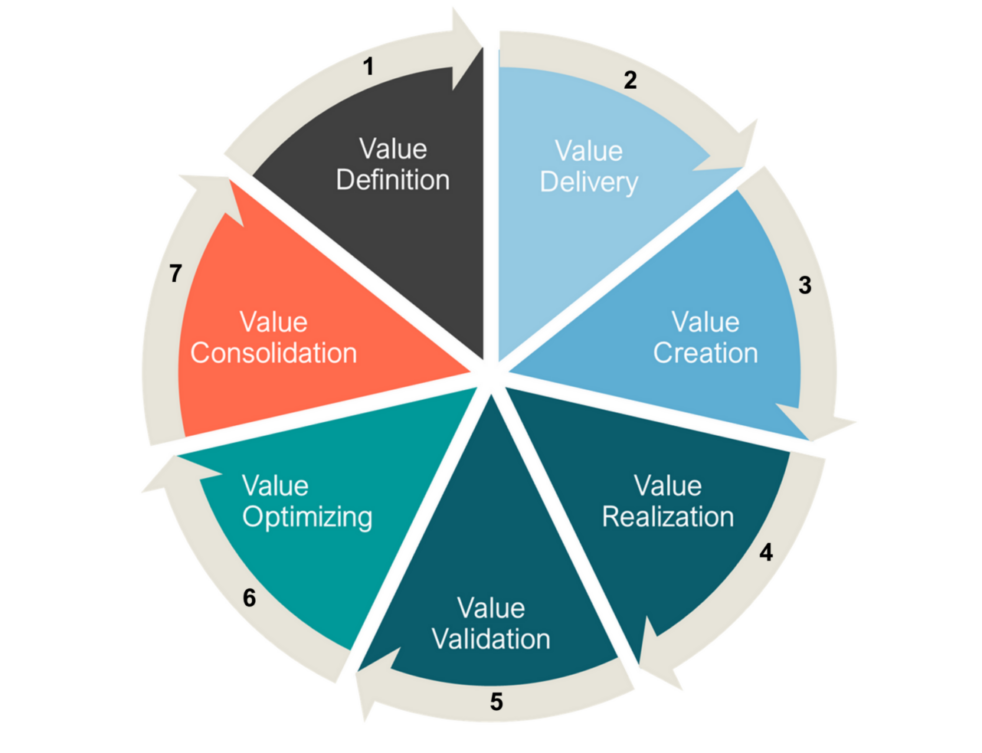
Insights
We explore the evolution of Microsoft's channel strategy over the past ten years, and what can be learned by viewing it through a Value Cycle lens.

Guides and eBooks
The Microsoft Fabric Partner Guide curates our recent articles, videos and resources to accelerate Crayon partner learning.

Insights
Support your cybersecurity game plans with our top picks of new and updated risk and resilience resources.

Webinars Series
Blogs
Crayon cloud security assessments help partners lock down M365 and Azure environments and build profitable cybersecurity practices. Learn how.
March 26, 2025
Nitro APAC Partner Awards 2024, Emerging Partner of the Year, Asia Pacific
2024
2024 Microsoft Partner of the Year Award - Business Transformation (Copilot)
October 3, 2023
FY23 MS Channel Growth Partner (Malaysia)
2021
Winner of the Channel Asia Women in ICT Awards
2021
Zoomtopia Partner Connect Award Winner 2021
2021
Winner of the Microsoft Cloud Solution Provider of the Year 2021
2021
Winner of the Laos 2021 Microsoft Partner of the Year Award
2021
Winner of the Microsoft APAC Services Partner of the Year
2021
Winner of Channel Asia Innovation Awards 2021
2020
Winner of the Veeam 2020 Aggregator of the Year Award

Connect Data Protection to strategic objectives via this Whitepaper

What are the most critical business objectives and solution adoption priorities for SMBs in our region? Download the latest Forrester study to find out!

Our APAC channel business is now part of a global organisation. That means there is a whole new world of value on offer for our partners. We can help you to tap into all of it.